Salah satu cara untuk mengecek keaslian sebuah Site adalah dengan memeriksa usia domainnya. Cek umur domain dengan berbagai Instrument seperti Wayback Machine dan WHOIS untuk mengetahui sejak kapan Internet site tersebut telah beroperasi.
Phishing is a variety of cyberattack that makes use of email (common phishing), mobile phone (vishing or voice phishing) or text (smishing or SMS phishing) to entice folks into delivering personal or sensitive information to cybercriminals. This info can vary from passwords, bank card facts and social security quantities to facts about an individual or a corporation.
Microsoft 365 Outlook - Using the suspicious message selected, choose Report information with the ribbon, then select Phishing. This can be the swiftest approach to report it and take away the information from your Inbox, and it will enable us boost our filters so that you see fewer of such messages Later on. To find out more see Use the Report Concept insert-in.
Site penipu seringkali memiliki tampilan yang buruk dan kurang profesional, mulai dari template yang berantakan, tata bahasa kurang tepat hingga banyak iklan yang mengharuskan diklik.
“Usain Bolt and Shelly have, and will go on to generate a huge selection of observe stars. We need a similar crystal clear path for other Occupations documented and Modern society supporting them on the Group degree.”
The call solicits the sufferer to answer validate their identity, As a result compromising their account qualifications.
Whilst Lots of individuals proceed to slide sufferer to ripoffs the US Embassy in Kingston has warned that if It appears as well very good for being correct, it can be in truth not correct.
E-mail Phishing: Phishing emails in many cases are the primary to come to intellect when people today listen to the time period phishing. Attackers deliver an illegitimate e mail asking for personal data or login credentials.
Cybercriminals typically faux to generally be trustworthy corporations, mates, or acquaintances in the fake message, which has a connection to a phishing Web site.
Never click any one-way links or attachments in suspicious email messages or Groups messages. If you get a suspicious message from a corporation and worry the information may be respectable, go for your web browser and open a completely new tab. Then go to the organization's Internet site from the individual saved beloved, or by way of a web lookup.
Below is a fantastic KnowBe4 useful resource that outlines 22 social engineering red flags frequently seen in phishing e-mails. We suggest printing out this PDF to go alongside to loved ones, buddies, and coworkers.
Cybercriminals proceed to hone their current phishing expertise and create new sorts of phishing frauds. Prevalent kinds bokep of phishing assaults contain the subsequent:
They use an array of tales to test to trick not only These accomplishing their best to Get well, but also anyone who attempts to assist. The obvious way to avoid these catastrophe-chasing scammers? Determine what their methods have in common.
Malicious actors could also pose like a supervisor, CEO or CFO over the telephone by using an AI voice generator and after that demand a fraudulent transfer of money. Whilst the worker thinks They are building a company transaction, they're truly sending money for the attacker.
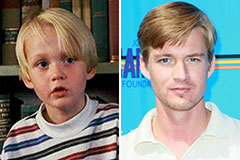 Mason Gamble Then & Now!
Mason Gamble Then & Now! Patrick Renna Then & Now!
Patrick Renna Then & Now! Jennifer Love Hewitt Then & Now!
Jennifer Love Hewitt Then & Now! Kenan Thompson Then & Now!
Kenan Thompson Then & Now! Loni Anderson Then & Now!
Loni Anderson Then & Now!